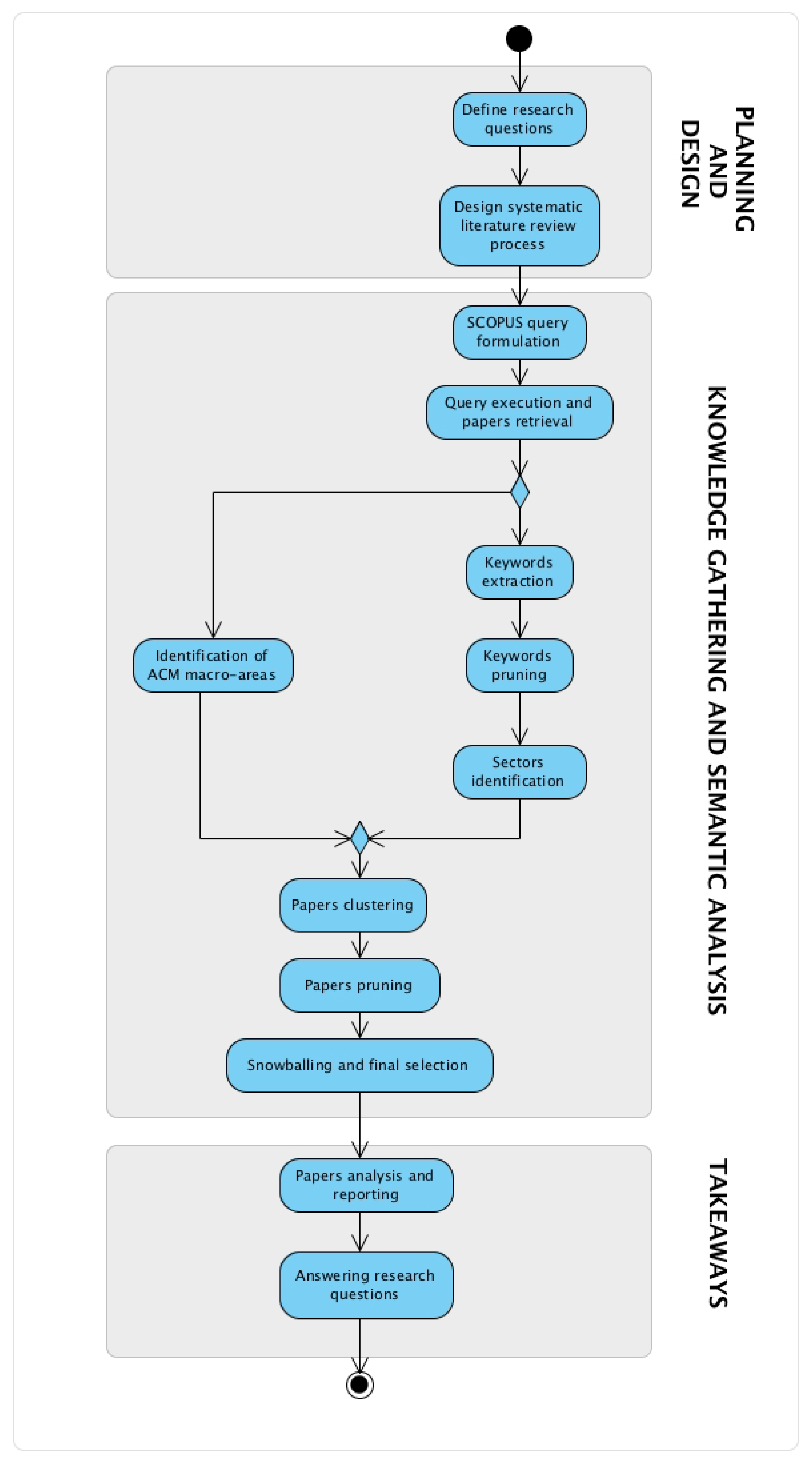
Compliance checking of software processes: A systematic literature review - Castellanos Ardila - 2022 - Journal of Software: Evolution and Process - Wiley Online Library
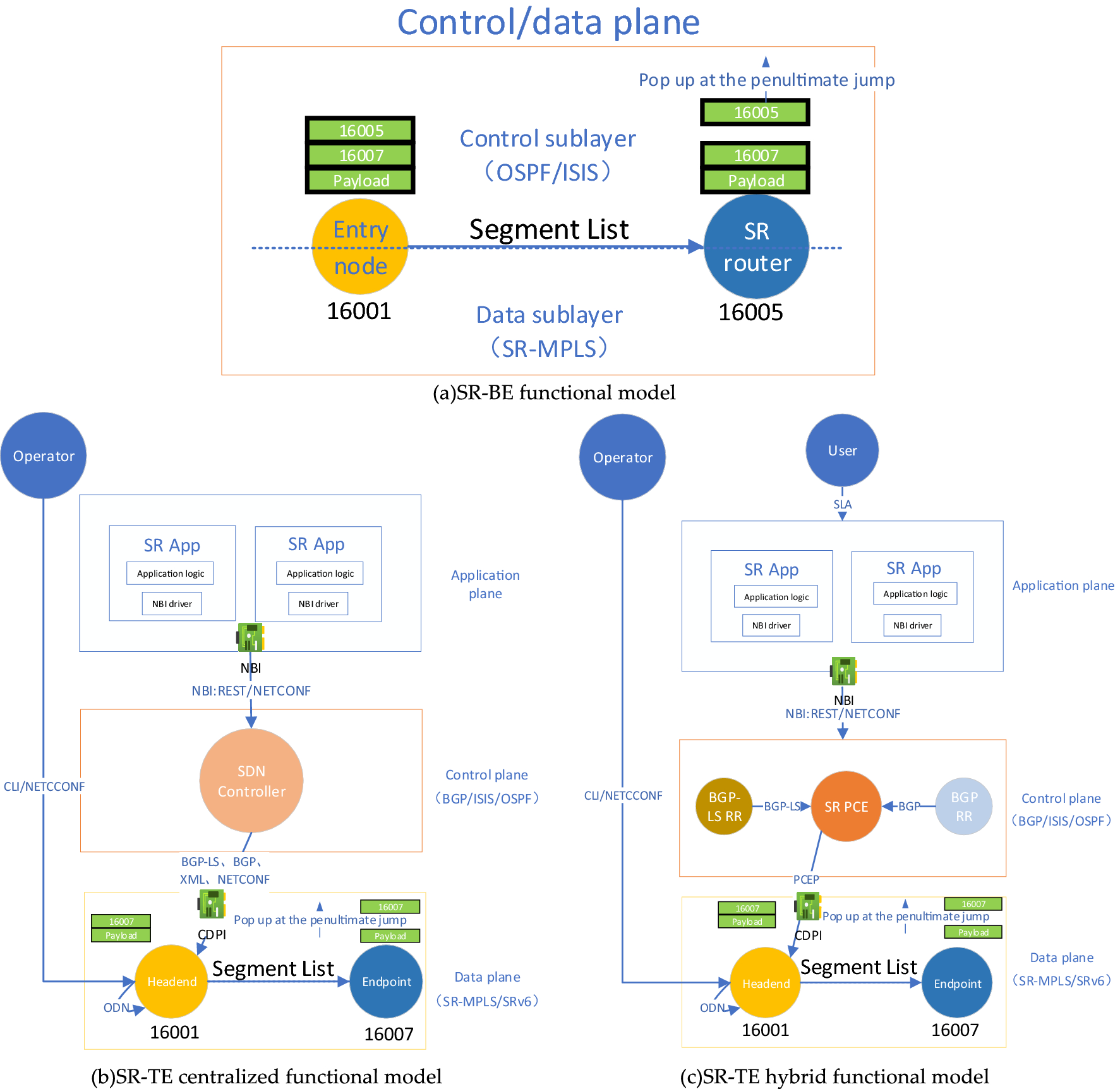
A data plane security model of segmented routing based on SDP trust enhancement architecture | Scientific Reports
Sustainability | Free Full-Text | Smart City Ontologies and Their Applications: A Systematic Literature Review

Securing Apache Kafka is easy and familiar with IAM Access Control for Amazon MSK | AWS Big Data Blog
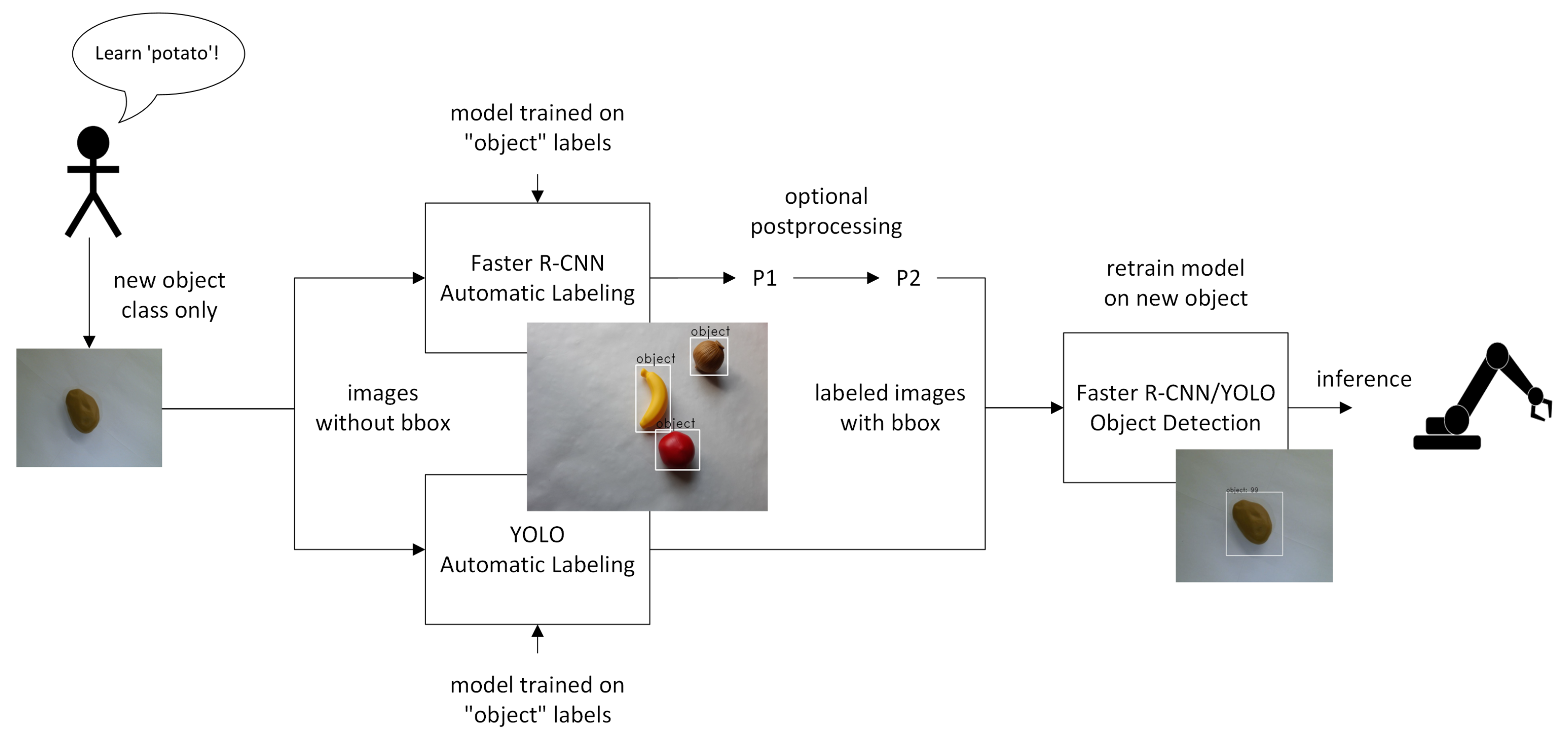
Micromachines | Free Full-Text | Automatic Bounding Box Annotation with Small Training Datasets for Industrial Manufacturing
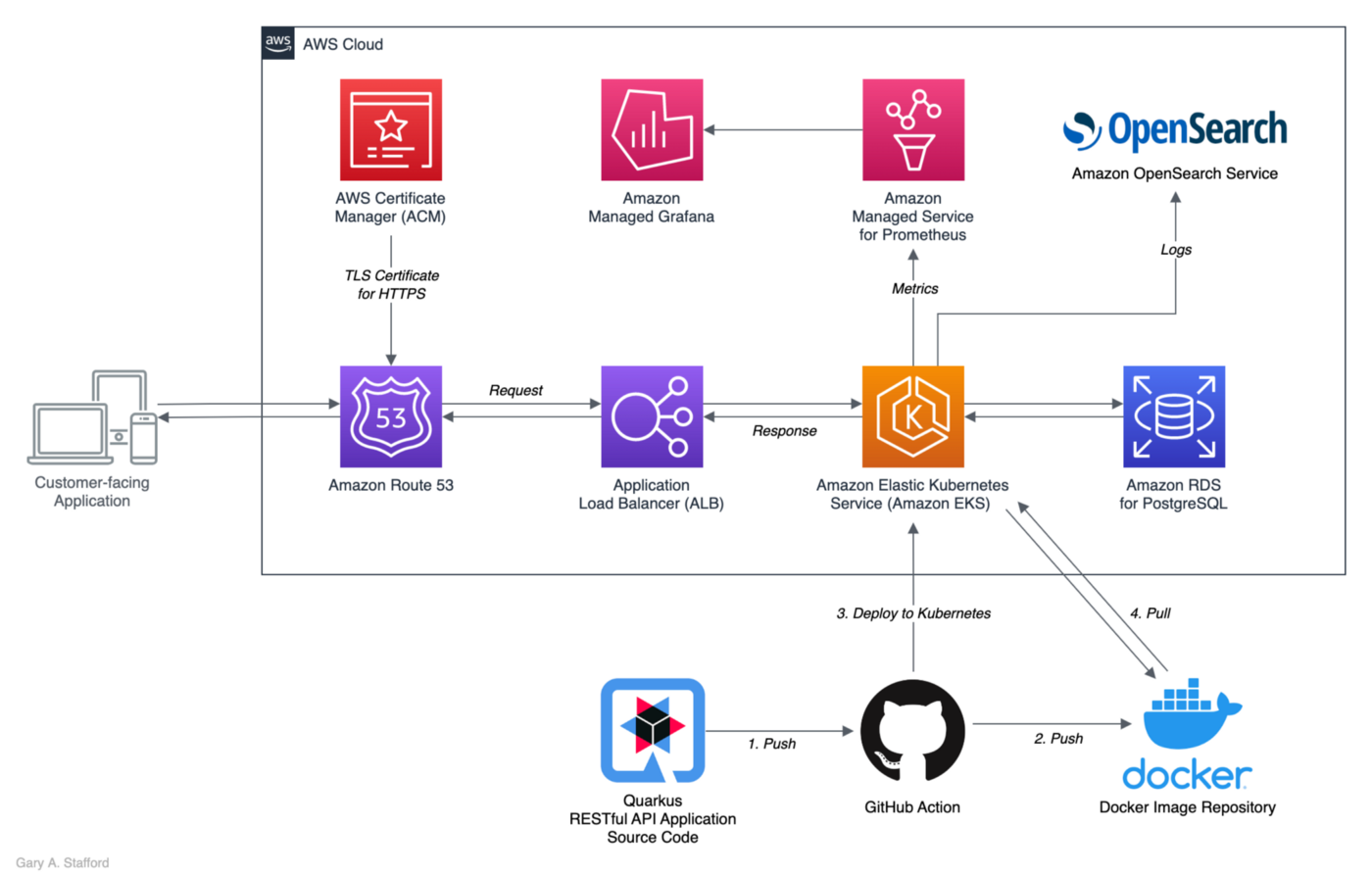
Building and Deploying Cloud-Native Quarkus-based Java Applications to Kubernetes | Programmatic Ponderings
Proceedings of the 29th annual international ACM SIGIR conference on Research and development in information retrieval: Evaluati

Inq, a Modern GPU-Accelerated Computational Framework for (Time-Dependent) Density Functional Theory | Journal of Chemical Theory and Computation

A program-driven simulation model of an MIMD multiprocessor | Proceedings of the 24th annual symposium on Simulation

Migrating connected device fleets to AWS with Custom Domains for AWS IoT Core | The Internet of Things on AWS – Official Blog

6 WHAT IS COMPUTER SCIENCE AND ENGINEERING? | Computing the Future: A Broader Agenda for Computer Science and Engineering |The National Academies Press

Interactive Programming for Parametric CAD - Mathur - 2020 - Computer Graphics Forum - Wiley Online Library